I’ll share some amazing methods to find the origin IP of any website protected by a Web Application Firewall (WAF).
Introduction
Web Application Firewalls (WAFs) are often used to improve security by hiding a website’s true IP address, which adds a strong layer of protection but can make security assessments and bug bounty testing more difficult. By identifying the source IP address, you can bypass these layers of protection and assess the server directly, This can uncover vulnerabilities that your WAF or CDN may have hidden.
Let’s explore advanced methods for uncovering source IP addresses and Performing detailed security checks
WAF Reconnaissance
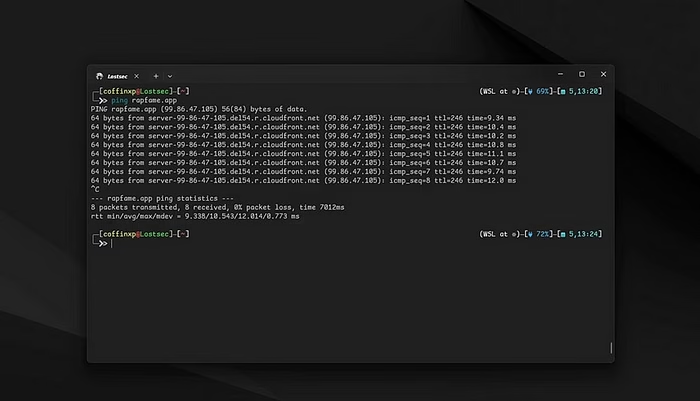
The first thing you should always do is check if your target has a web application firewall. There are a few easy ways to do this, but the first thing you should do is ping your target. It will show you all the information about the IP address, you can see in the screenshot, the IP address is pointing to the CloudFront server, which means its behind the WAF.
check by extension:
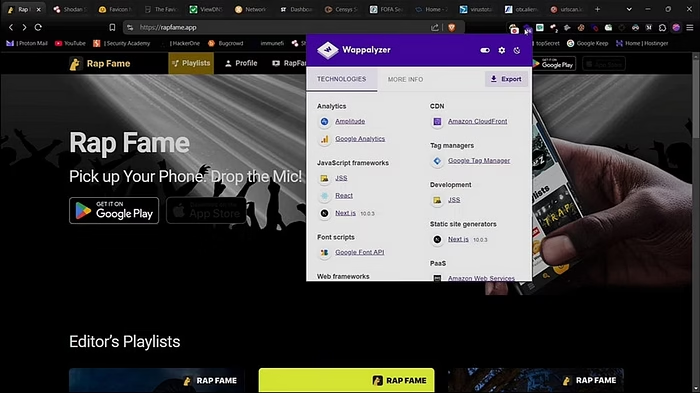
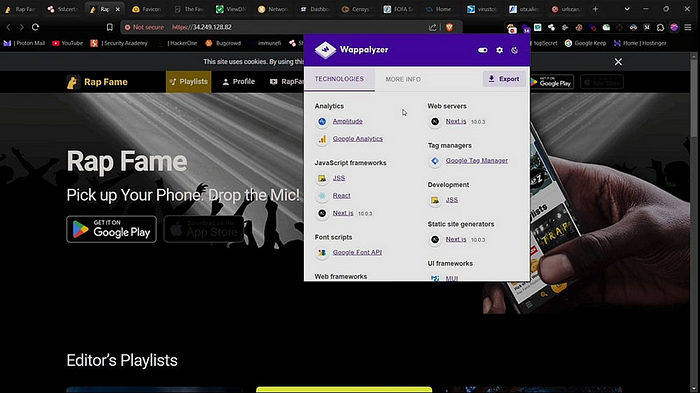
You can use the Wappalyzer extension to check if a site has a WAF. Visit the website and check if it uses a CDN such as Cloudflare, Amazon CloudFront, or Akamai. as you can see in the screenshot it uses Amazon CloudFront CDN.
WafWOOf tool:
To cross-verify, you can also use the WafWOOf tool to identify the waf used you can see in the screenshot its identified as Amazon Cloud Front waf.
Copywafw00f https://target.com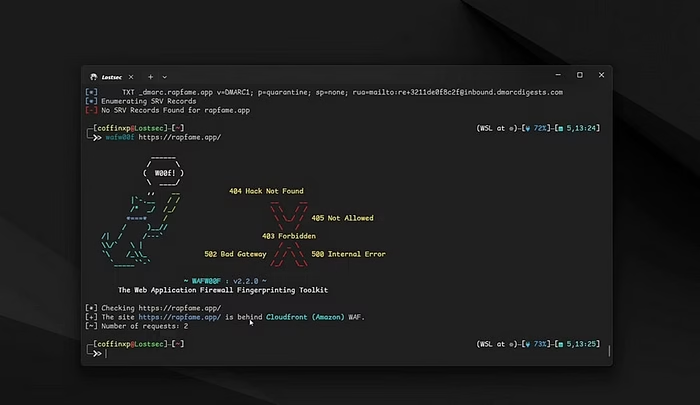
now let’s move on into finding the origin IP
Method #1 — Dnsrecon
Use the DNSRecon tool to perform a reverse DNS lookup. This method sometimes reveals the origin IP if the server lacks WAF protection..
Copydnsrecon -d target.com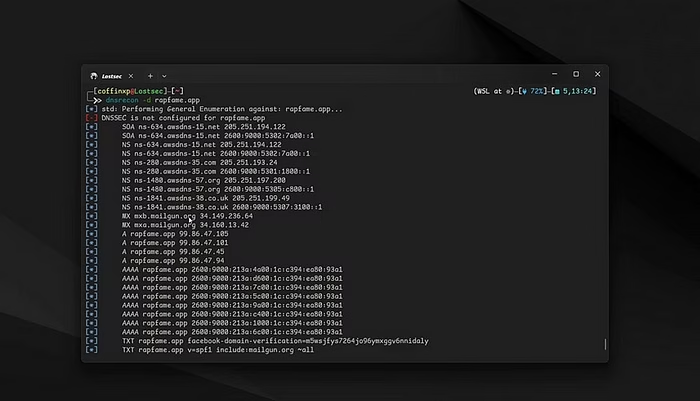
Method #2 — Shodan Dorks
The next thing I would recommend to find the origin IP is to use Shodan. It is also pretty easy to search for many leaked IPs by using a simple search. You can find all the IP addresses of the website.
CopySsl.cert.subject.CN:"<DOMAIN>" 200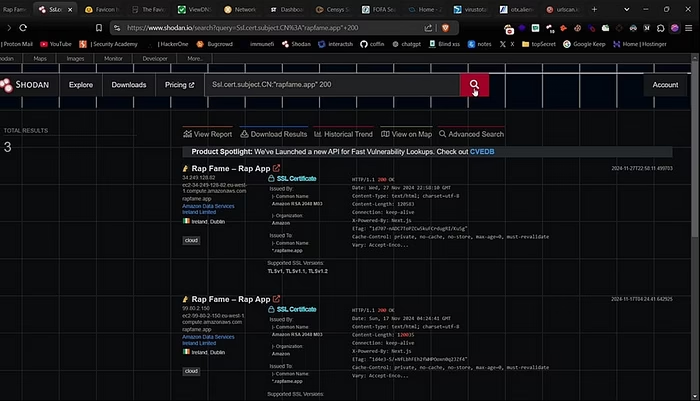
Also, using Shodan CLI with HTTPX tool will give you just the IP address with the status code, title, server, and technology details, so you can look at the title to figure out what IP addresses are working . Check each IP in your browser, if this is the origin ip you will see your site load fine without any WAF errors.
Copyshodan search Ssl.cert.subject.CN:"<DOMAIN>" 200 --fields ip_str | httpx-toolkit -sc -title -server -td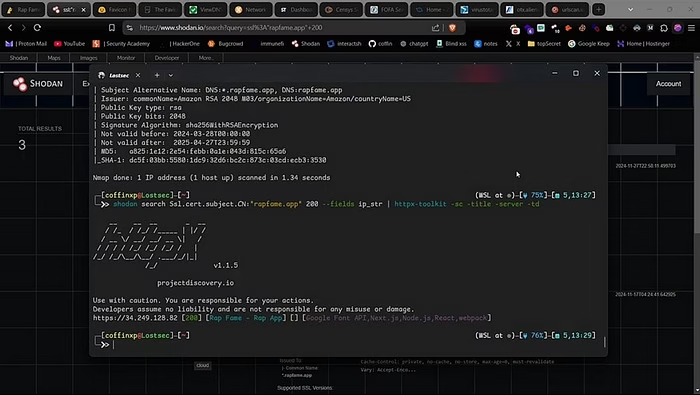
Method #3 — Censys
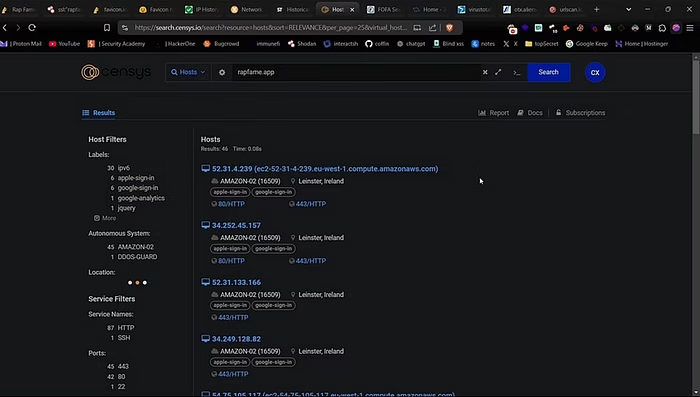
Another great tool for IP recognition is to use Censys search. Just paste your target in the search bar and you’ll get results with the ipv4 and ipv6 address. Look for the IPv4 entries that mention the same SSL certificate or host details and open that up in the browser to check if it’s the origin IP or not.
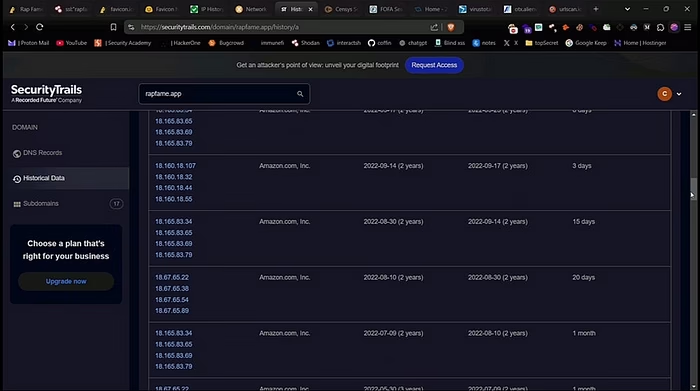
Method #4 — Security Trails
SecurityTrails is a powerful tool for analyzing historical IP records, which is especially useful when finding the originating IP address of a website. Just enter the website name in the search bar and select Historical Data, and all IP history will be displayed. Open these IPs one by one to see if you can access them directly.
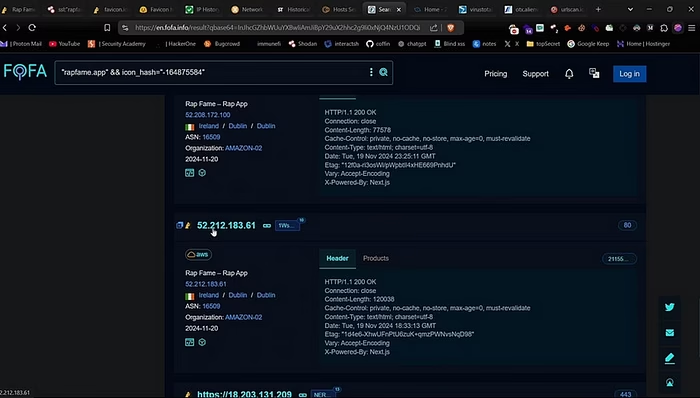
Method #5 — Fofa
We can use Fofa, another excellent tool to find IP addresses. Just paste the domain and click on search. There will be lots of results. Just filter it with site favicon hash and it gives you more cleaned results.
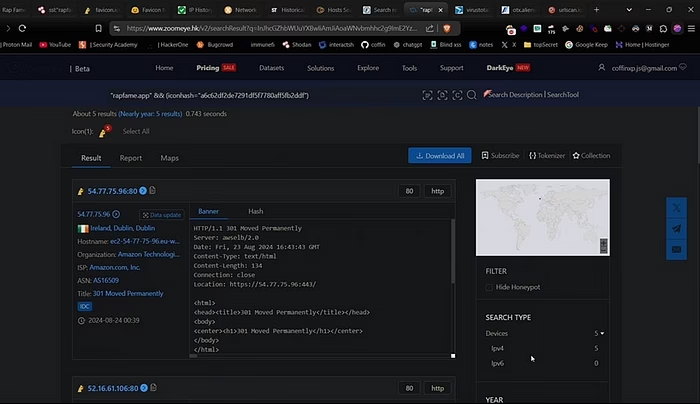
Method #6 — Zoomeye
ZoomEye is another great alternative to Shodan. Enter the domain and click on the search button. And Filter it by the favicon hash. Then filter by IPv4 address for clean results. After that open these IPs one by one to see if it’s the origin IP or not.
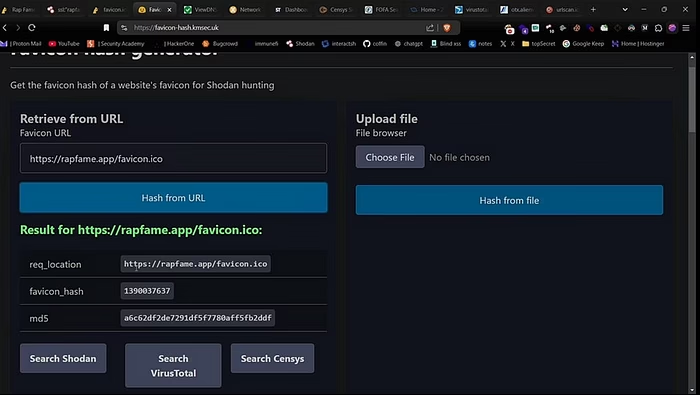
Method #7 — Favicon Hash
Most sites have a unique favicon (the little icon in your browser tab). This icon can be hashed to find other servers using the same icon. First, find the favicon URL of the target website using the website favicons.teamtailor-cdn.com, then enter the target website and it will extract the favicon URL. Once you have the URL, find its hash using the favicon-hash.kmsec.uk website. then you can search for the hash on Shodan and Censys to see if it matches the IP address associated with the target domain.
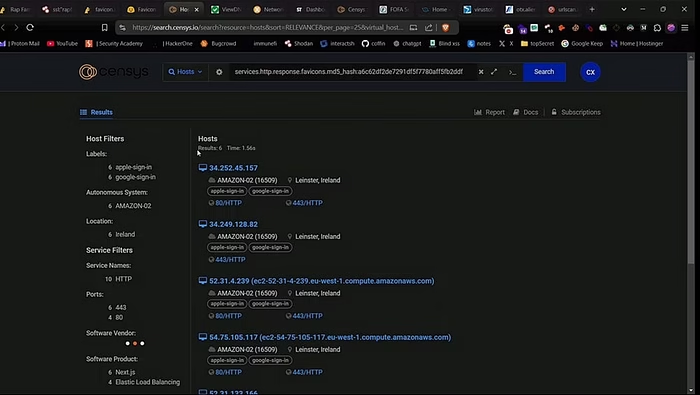
Method #8 — viewdns.info
You can also check the IP history of the website using a view DNS info website. Just Enter the domain, and you’ll see a list of historical IPs. You can test these IPs one by one to find the origin ip for different domains.
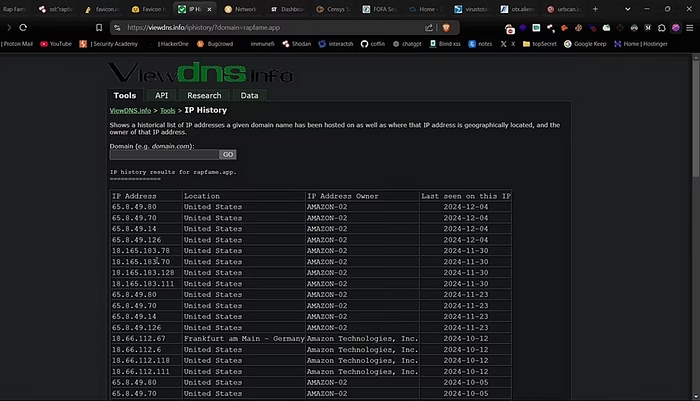
Method #9 — SPF records
Another website to try is checking the SPF record of a domain. Just copy the domain paste it on the search bar and select spf record. You will see all the IP addresses of the domain that could potentially point to the origin IP. You can test these IPs similarly.
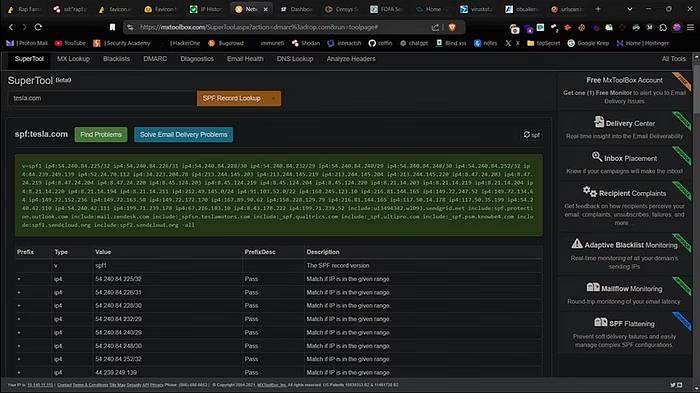
Method #10 — VirusTotal
Another effective method is to use VirusTotal, a great tool for discovering subdomains and their associated IP addresses. I created a simple one-line command to gather all the IP addresses from the website with title and server information.
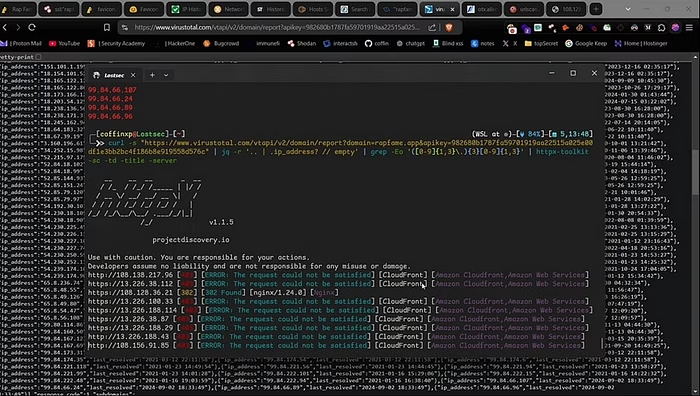
Method #11 — AlienVault
Now move on to the next method. You can also use Alien Vault to find the origin IP of the website. I made oneliner for this just copy this oneliner and paste it on the terminal change the domain name that u want and hit enter. You will see all IP addresses of the site along with the title and server information.
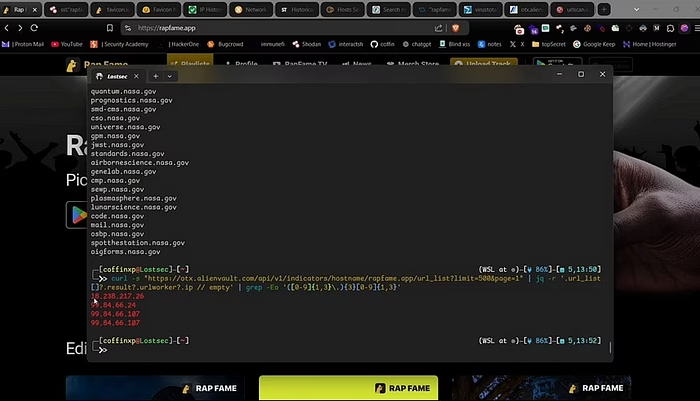
Combining VirusTotal and AlienVault with bash script:
For an even easier solution, I have created a bash script that fetches unique IPs from VirusTotal and AlienVault and removes duplicates. Just enter this bash command with a domain you want the IP address, and hit enter. You will see all unique IP addresses from these both sources and also the saved result in the txt file. Just use httpx on it, and it will show all IP address information with title and server information.
Copy#!/bin/bash
# API keys (replace with your own keys)
VT_API_KEY="<api_key>"
# Function to fetch IP addresses from VirusTotal
fetch_vt_ips() {
local domain=$1
curl -s "https://www.virustotal.com/vtapi/v2/domain/report?domain=$domain&apikey=$VT_API_KEY" \
| jq -r '.. | .ip_address? // empty' \
| grep -Eo '([0-9]{1,3}\.){3}[0-9]{1,3}'
}
# Function to fetch IP addresses from AlienVault
fetch_otx_ips() {
local domain=$1
curl -s "https://otx.alienvault.com/api/v1/indicators/hostname/$domain/url_list?limit=500&page=1" \
| jq -r '.url_list[]?.result?.urlworker?.ip // empty' \
| grep -Eo '([0-9]{1,3}\.){3}[0-9]{1,3}'
}
# Check if domain is provided
if [ -z "$1" ]; then
echo "Usage: $0 <domain_name_or_url>"
exit 1
fi
DOMAIN=$1
OUTPUT_FILE="${DOMAIN}_ips.txt"
# Get IPs from both sources, remove duplicates, and save to file
echo "Collecting IP addresses for: $DOMAIN"
{
fetch_vt_ips $DOMAIN
fetch_otx_ips $DOMAIN
} | sort -u | tee "$OUTPUT_FILE"
echo "-------------------------"
echo "IP addresses saved to: $OUTPUT_FILE"Final verification:
Now, for the final verification, you can put the origin IP that you found in the/etc/hosts file with its domain name and save it, and search the domain on the browser it will now load the site with your origin IP you can also use the ping command to check which IP it’s resolving from.
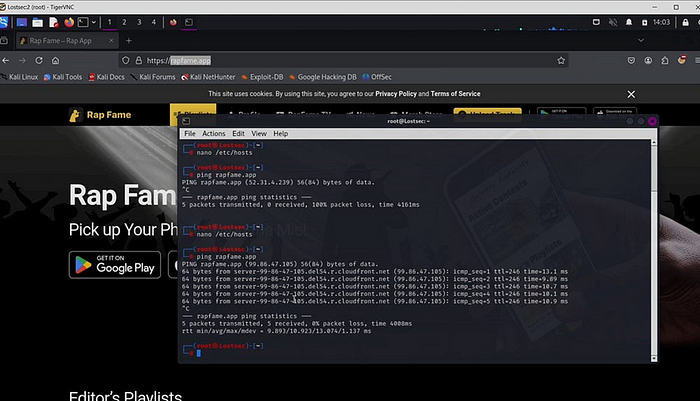
You can also use the nmap command to check the certificate and see if it’s points to the website’s domain or not
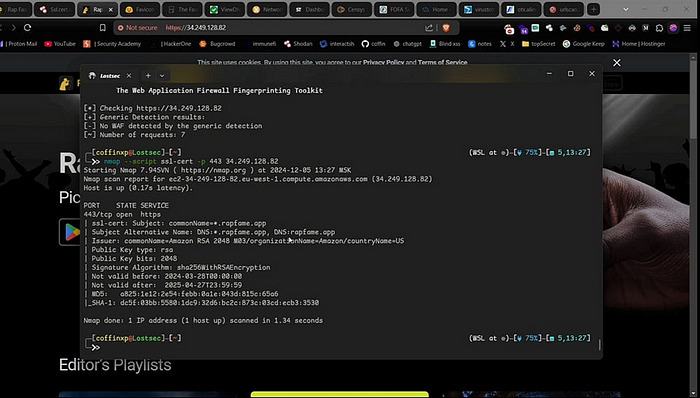
if you find the source ip and if you access it in the browser it will be displayed like this without any waf protection.
note: even if you found an IP and when you open it in the browser and it redirects to the main site, it does not mean that it is the original IP. The IP can be configured to point to the primary domain via DNS, even if it does not host the actual content of the site. Many CDNs or WAFs are designed to redirect traffic from the edge servers to the primary domain while still masking the real origin IP. The IP you accessed may belong to the CDN or WAF infrastructure rather than the backend server
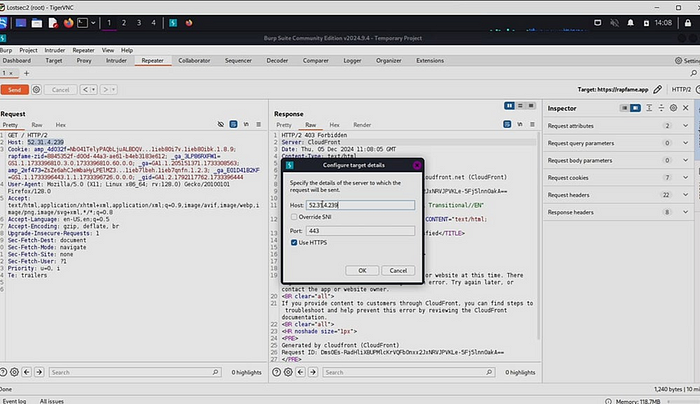
To test the site in Burpsuite, just copy the IP address from the hostname into both of the options in the provided screenshot. This way you will get the results by the original IP address without any WAF security. From now on, you can easily test any vulnerabilities in the site.
Tips for Bug Bounty Hunters
If you have any origin IP then don’t rush to report that. Explore the possibilities for vulnerabilities such as SQL injection and XSS to increase the effects. Since there is no WAF on the origin IP, the chances of finding a bug increase. Hope all of these methods will help you on your bug-hunting journey.
Conclusion
Finding a website’s origin IP is key to bypassing WAFs and CDNs for deeper security testing. This guide covered tools like Shodan, Censys, and VirusTotal, and methods such as favicon hash lookups and SPF checks to streamline the process. I hope these tips help in your bug bounty or cybersecurity journey. Stay tuned for more tutorials to enhance your skills!







Leave a Comment
You must be logged in to post a comment.